Cyberattack is one of the fastest growing crimes in the world, we have seen passwords being leaked regularly, local administrator account is like God of machine, it has superpower to do anything for the machine. A lot of IT guys simply use the same password for all local administrator accounts, the attacker easy access to the whole estate if one machine is breached.
Microsoft LAPS is one of solutions to prevent the issues, The “Local Administrator Password Solution” (LAPS) provides management of local account passwords of domain joined computers. Passwords are stored in Active Directory (AD) and protected by ACL, so only eligible users can read it or request its reset. Today, I am going to show you how to deploy it.
System prerequisites
Supported Operating System
Windows Server 2019, Windows Server 2008, Windows Server 2016, Windows 10, Windows Server 2012 R2, Windows Server 2003, Windows Server 2008 R2, Windows Server 2012, Windows 7, Windows 8, Windows Vista, Windows 8.1, Windows Server 2022
Active Directory: (requires AD schema extension)
• Windows 2003 SP1 or later.
Managed machines:
• Windows Server 2003 SP2 or later, or Windows Server 2003 x64 Edition SP2 or later.
Note: Itanium-based machines are not supported.
Management tools:
• .NET Framework 4.0
• PowerShell 2.0 or later
1.login to LAPS Management Server, download Microsoft LAPS Package from https://www.microsoft.com/en-us/download/details.aspx?id=46899
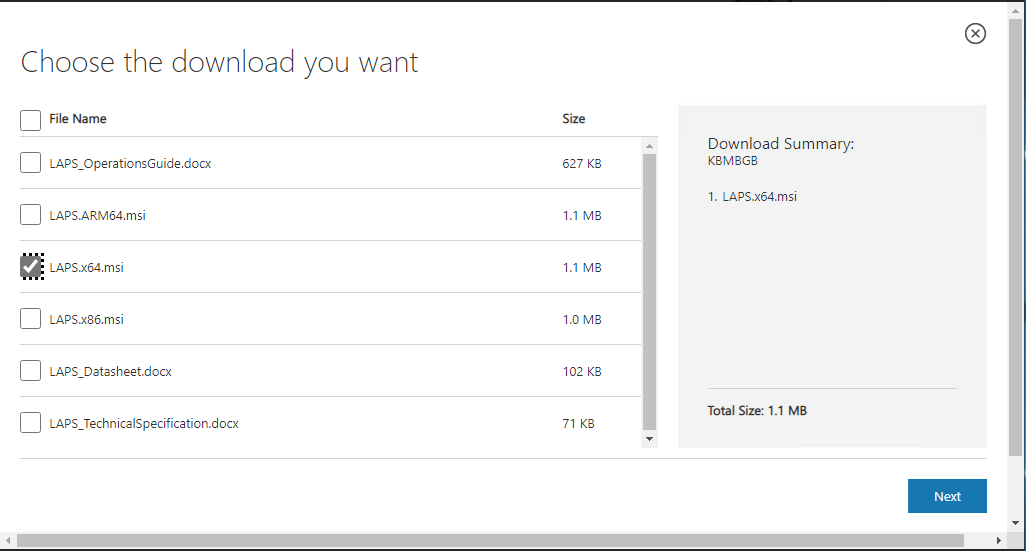
2.On the Choose the download you Want page, select LAPS.x64.msi, click Next.
3.Login to the target computers which will update the local administrator password.
4.Run LAPS.x64.msi file. (You need to run this as administrator).

5.On the Welcome page, click Next.

6.On the End-User License Agreement page, select I accept terms in the License Agreement, click Next.
7.On the Custom Setup page, deselect AdmPwd GPO Extension and select Management Tools. If you also managing the local administrator account of the management server, you also need to install AdmPwd GPO Extension. In my case, I am installing it in a Domain controller so I do not need it.
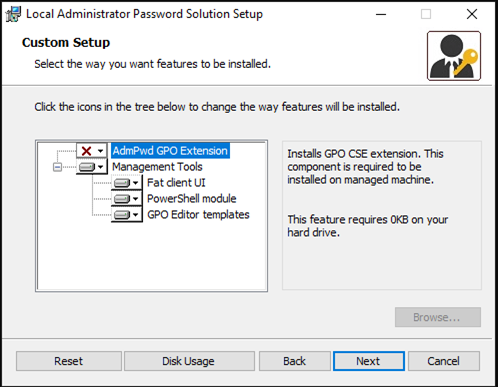
8.Click Next.

9.On the Ready to install Local Administrator Password Solution page, click Install.
10.On the Completed page, click Finish.
Once this is done, we need to Active Directory schema to support Microsoft LAPS
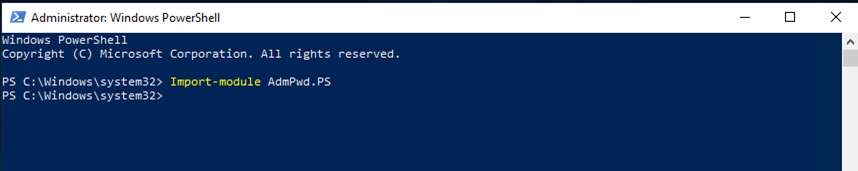
11.Open PowerShell as Active Directory Schema Administrator.
12.Run below cmdlet.
Import-module AdmPwd.PS
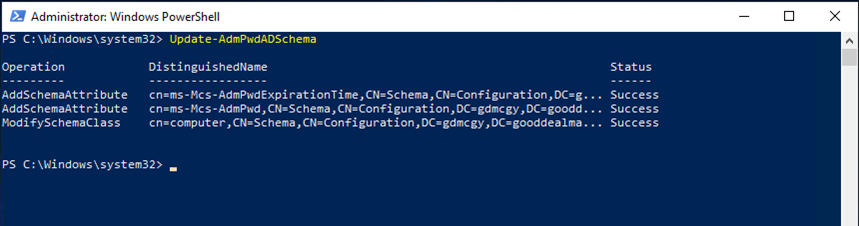
13.Run below cmdlet to update the schema.
Update-AdmPwdADSchema
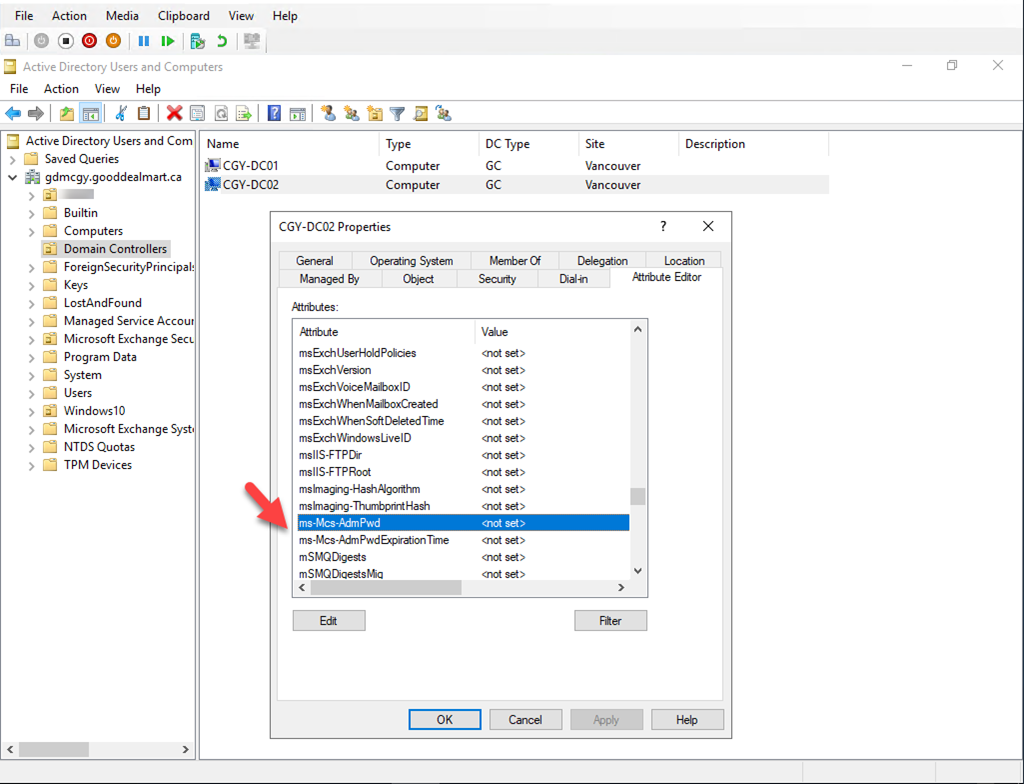
14.Verify two new attributes in the computer object after schema update.
ms-Mcs-AdmPwd – Save the administrator password in clear text. ms-Mcs-AdmPwdExpirationTime – Save the timestamp of password expiration.
These values will be updated once we finish the rest of the configuration.
During the password update process, the computer object itself should have permission to write values to ms-Mcs-AdmPwd and ms-Mcs-AdmPwdExpirationTime attributes. To do that we need to grant permissions to SELF built-in account.
15.Open PowerShell as Domain Administrator.
16.Run below cmdlet to change computer object permissions.
Set-AdmPwdComputerSelfPermission -OrgUnit Servers
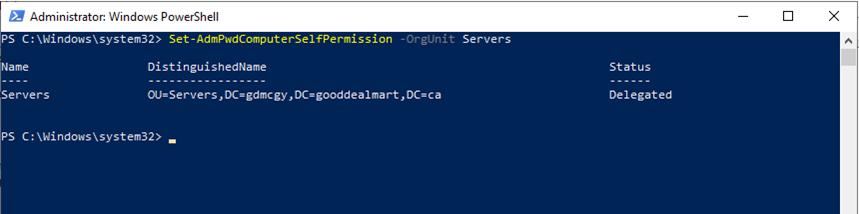
Servers is the OU I created for all the machine objects.
17.Creating a new security group and assign users as member of this group, the users of this security group have permissions to view the passwords for local administrators.
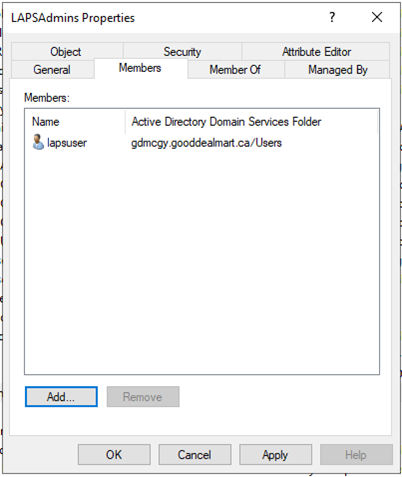
18.Before we assign permissions, run below cmdlet to see who had privileges to view the passwords by default.
Import-module AdmPwd.PS
Find-AdmPwdExtendedRights -Identity Servers
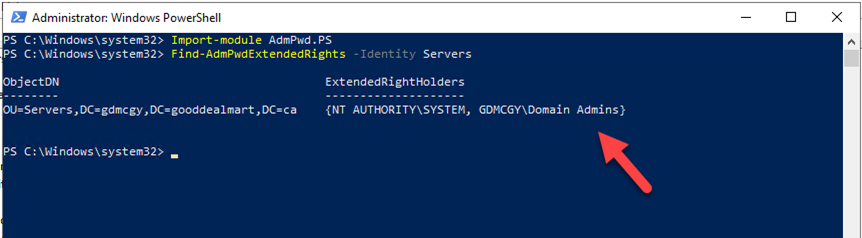
We noticed extended permissions are only applied to the Domain Admins group. It means a local administrator password for a computer object in Servers OU, can only access by a domain admin account.
19.Run below cmdlet to add extended permissions to LAPSAdmins security group.
Set-AdmPwdReadPasswordPermission -Identity Servers -AllowedPrincipals LAPSAdmins
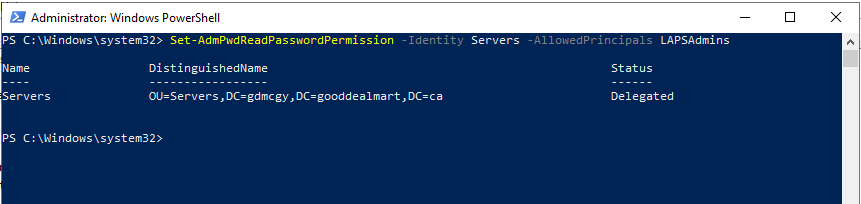
20.Run below cmdlet to verify extended permissions to LAPSAdmins security group.
Find-AdmPwdExtendedRights -Identity Servers | fl

21.Creating a GPO to install LAPS agent software in managed computers.
22.Log in to Domain Controller.
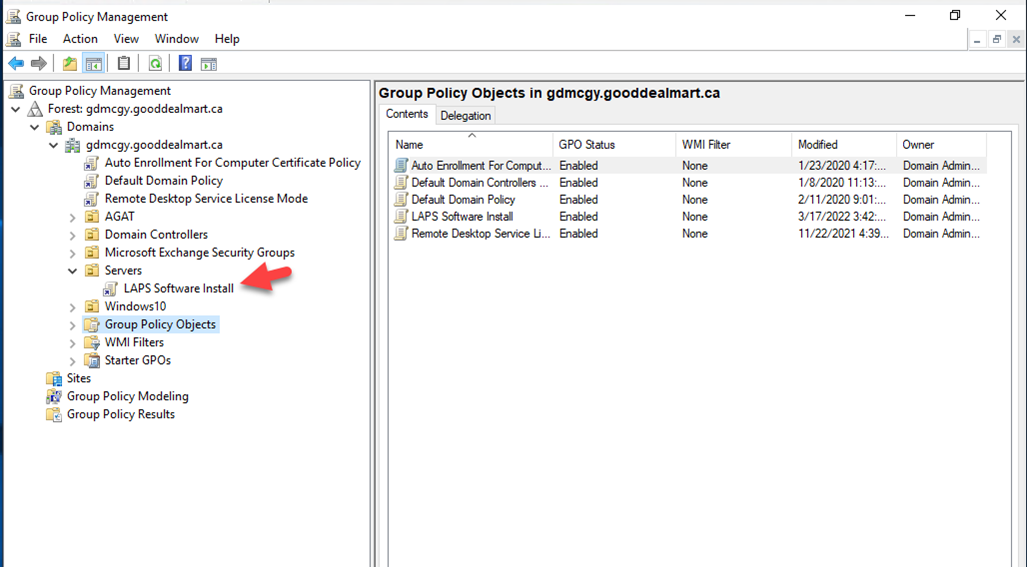
23.Open Group Policy Management.
24.On the Group Policy Management console, right-click Group Policy Objects, select New.
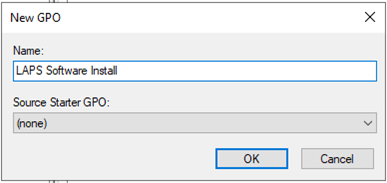
25.Type LAPS Software Install as the new gpo name, click OK.
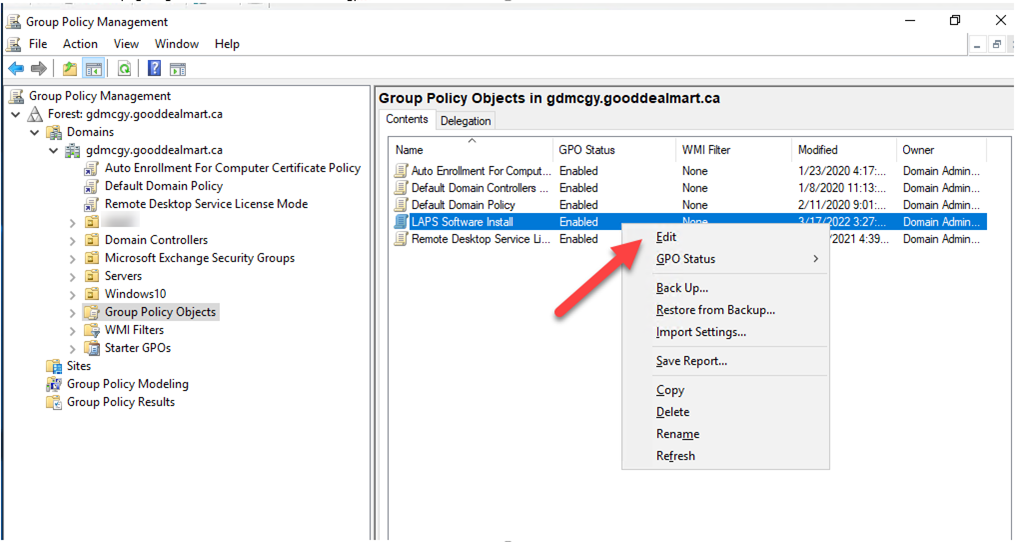
26.On the Contents page, right-click LAPS Software Install gpo, select Edit.
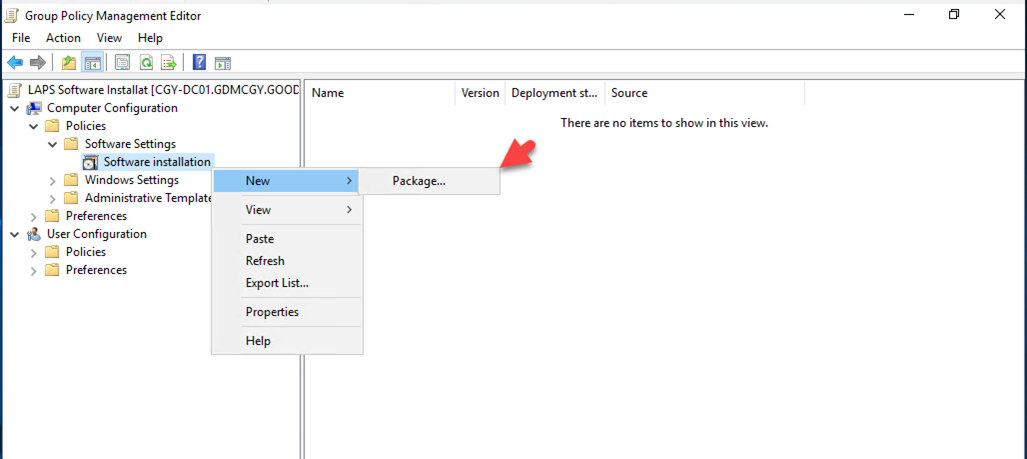
27.Go to Computer Configuration, then Policies, and then Software settings, right-click Software installation, select New and click Package.
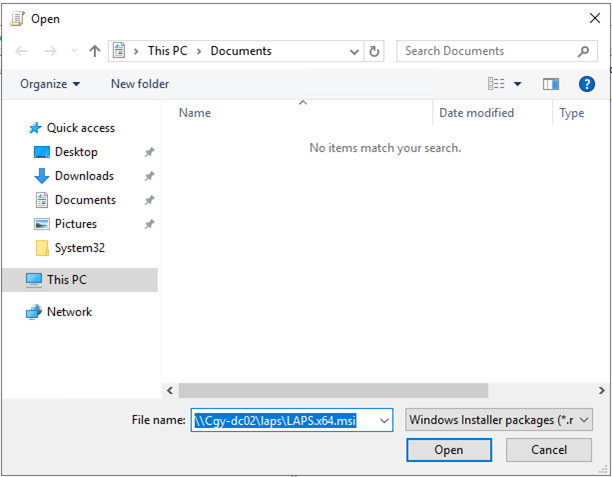
28.On the Open page, type \\Cgy-dc02\laps\LAPS.x64.msi as File name, click Open.
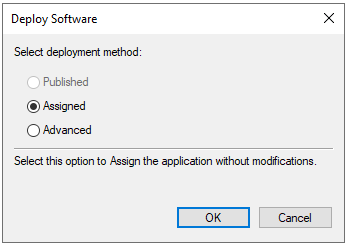
29.On the Deploy Software page, select Assigned, click OK.
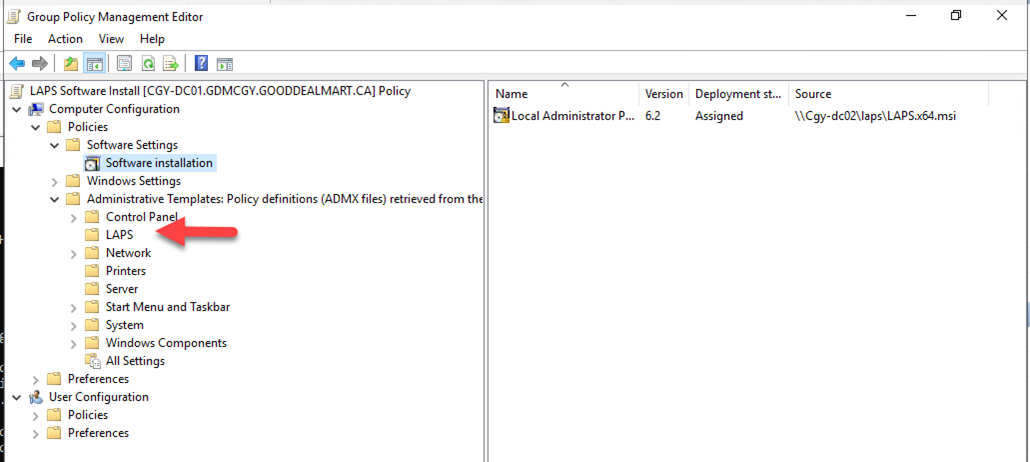
30.Go to Computer configuration, then Administrative Templates, and then LAPS.
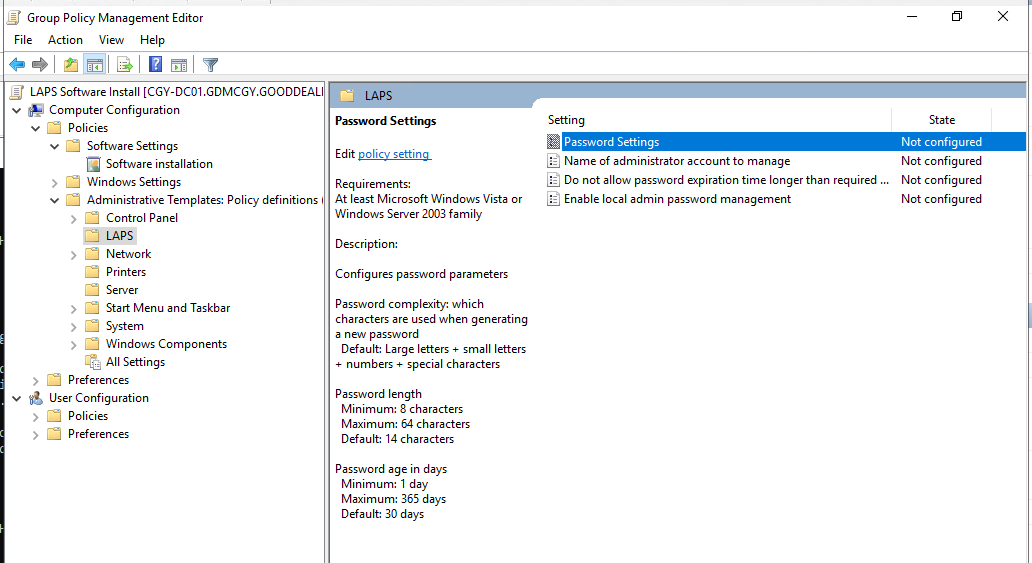
31.Double click on Password Settings.
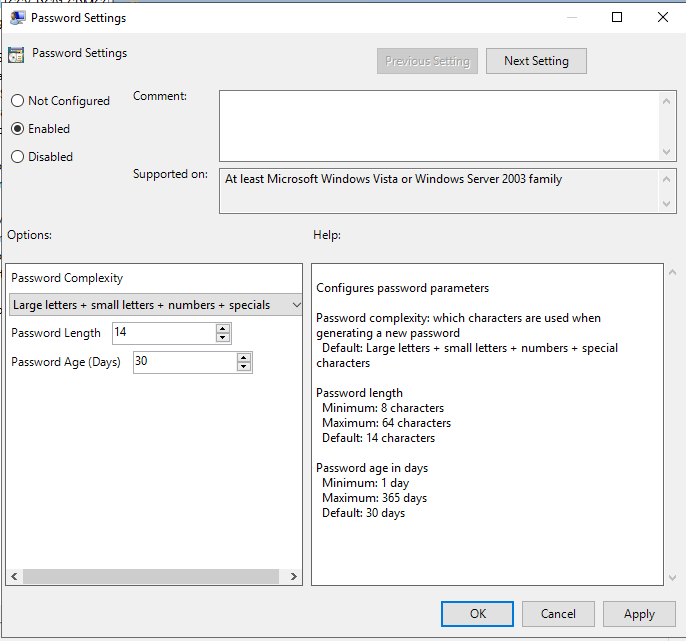
32.On the Password Settings page, select Enabled, you can define password complexity settings and password age at Options, click on OK.
33.Double click on the Do not allow password expiration time longer than required by policy.
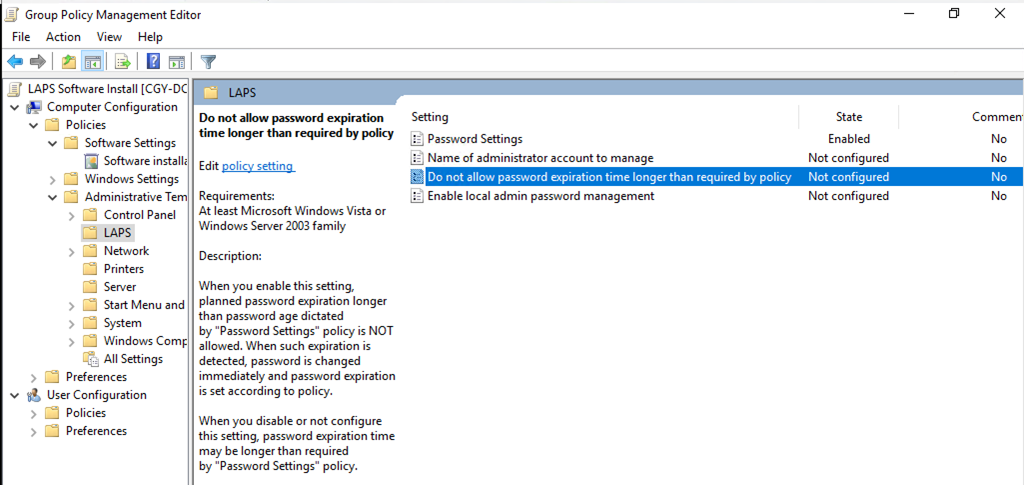
34.On the Do not allow password expiration time longer than required by policy, select Enabled, click OK.
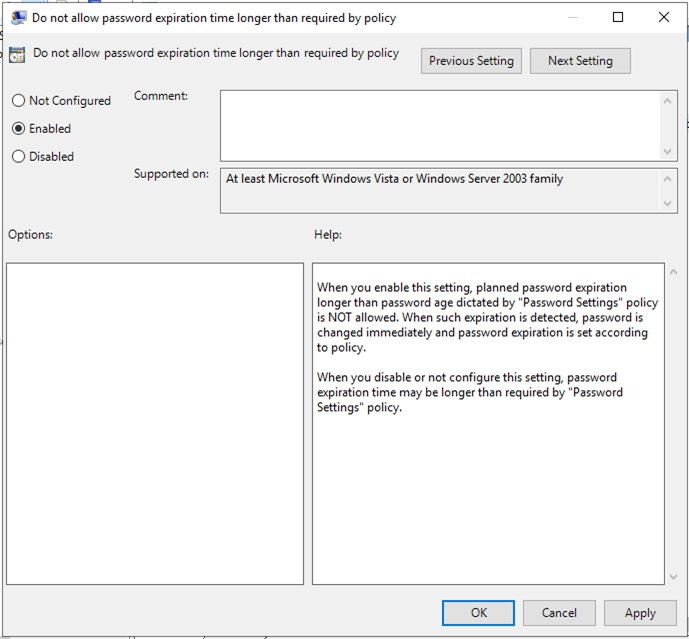
35.Double click on the Enable local admin password management.
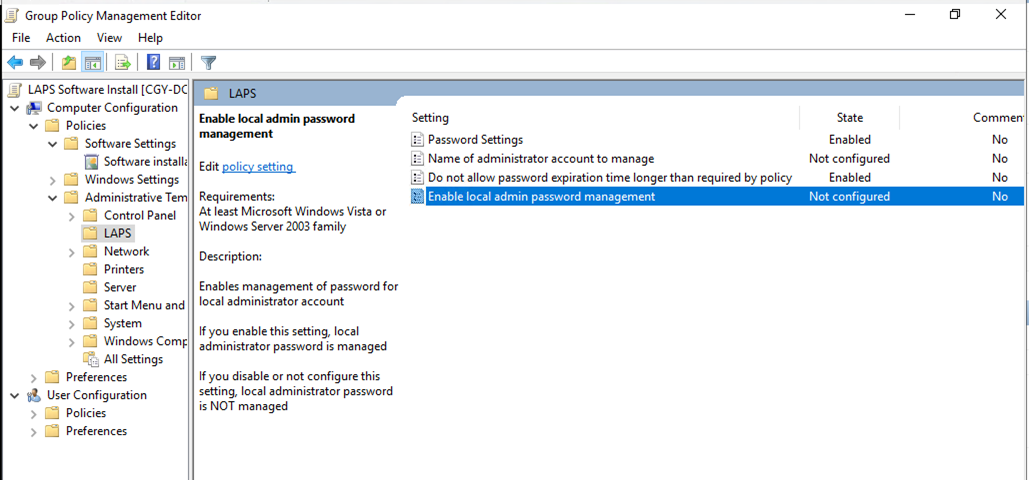
36.On the Enable local admin password management page, select Enabled, click OK.
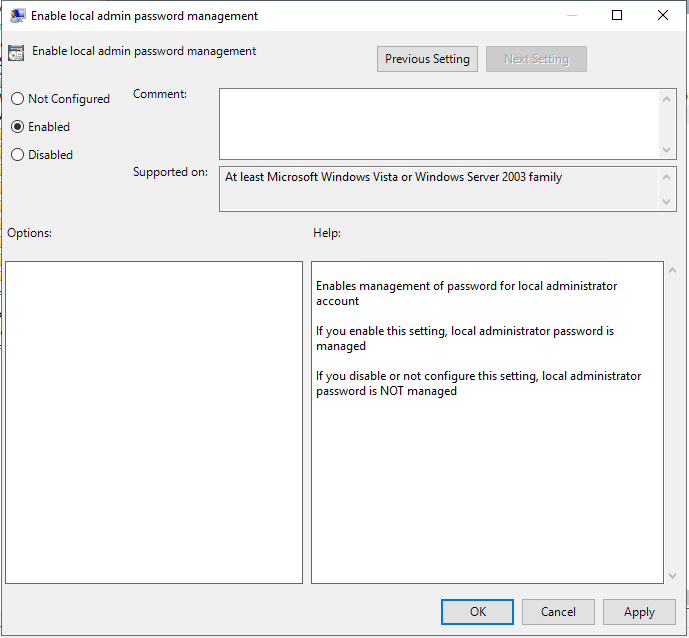
37Double click on the Name of administrator account to manage.
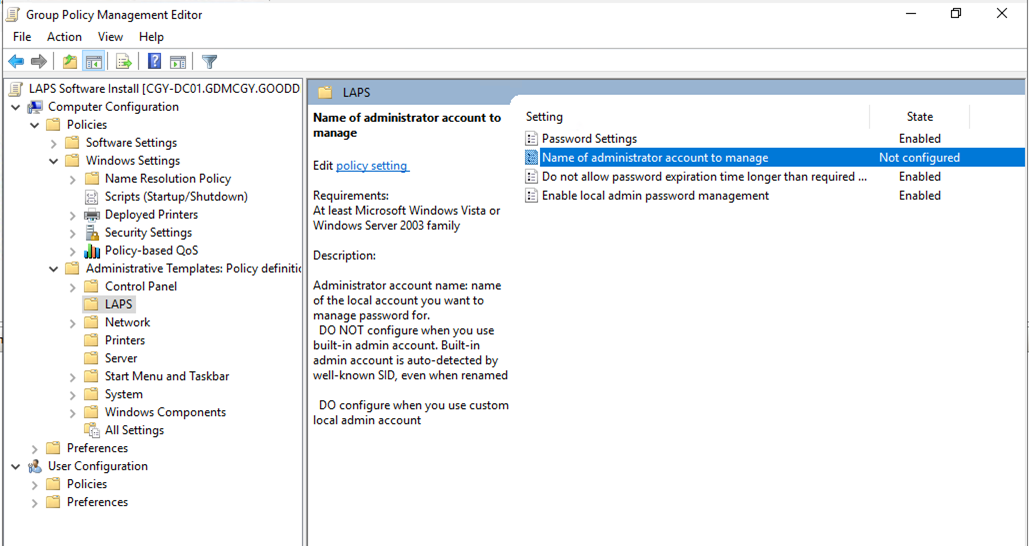
38.on the Name of administrator account to manage page, select Enable, enter admin as Administrator account name, click OK.
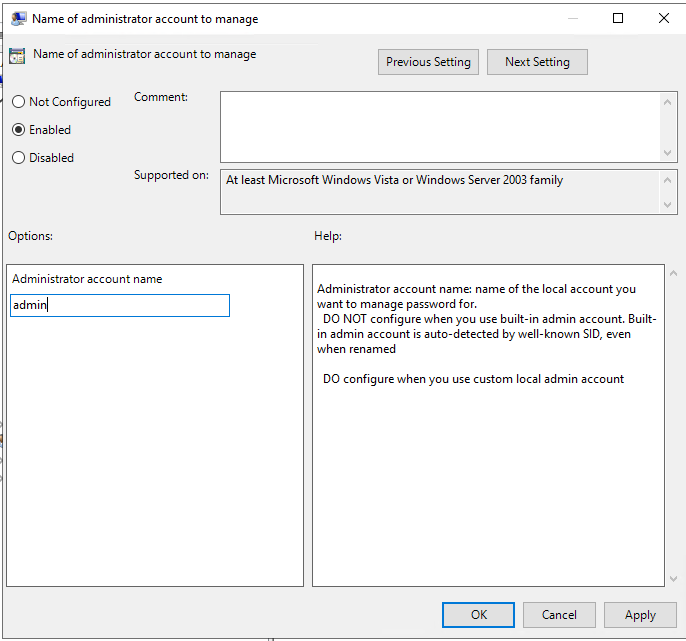
39.Close the Group Policy Management Editor.
40.On the Group Policy Management Console, right-click Servers OU, select Link an Existing GPO.
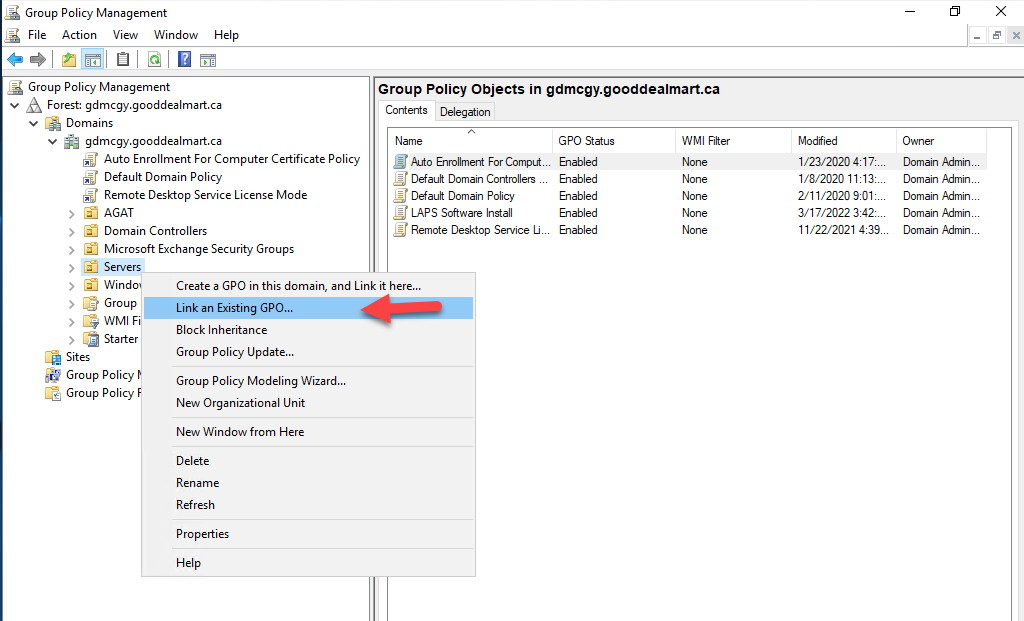
41.On the Select GPO page, select LAPS Software Install, click OK.
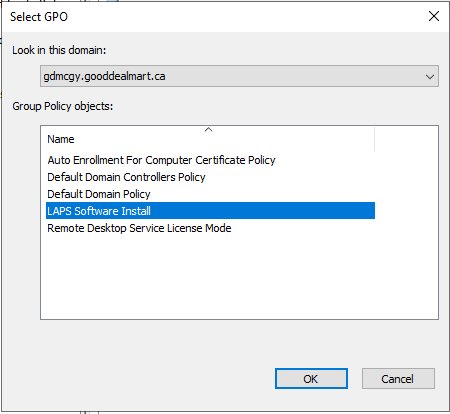
42.Close Group Policy Management console, this will push agents to the Computers under Servers OU. The installation is required a reboot on the computers to complete the installation.
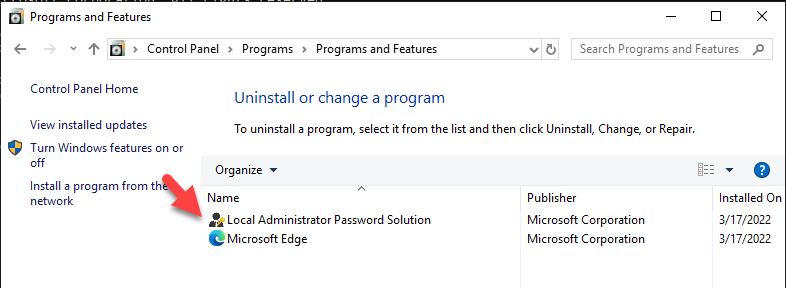
43.Login to member server of Servers OU, reboot the machine or run gpupdate.

44.Verify LAPS agent installed.
45.Login tp domain controller (LAPS manager server) as a member of LAPSAdmins group.
46.Open LAPS UI.
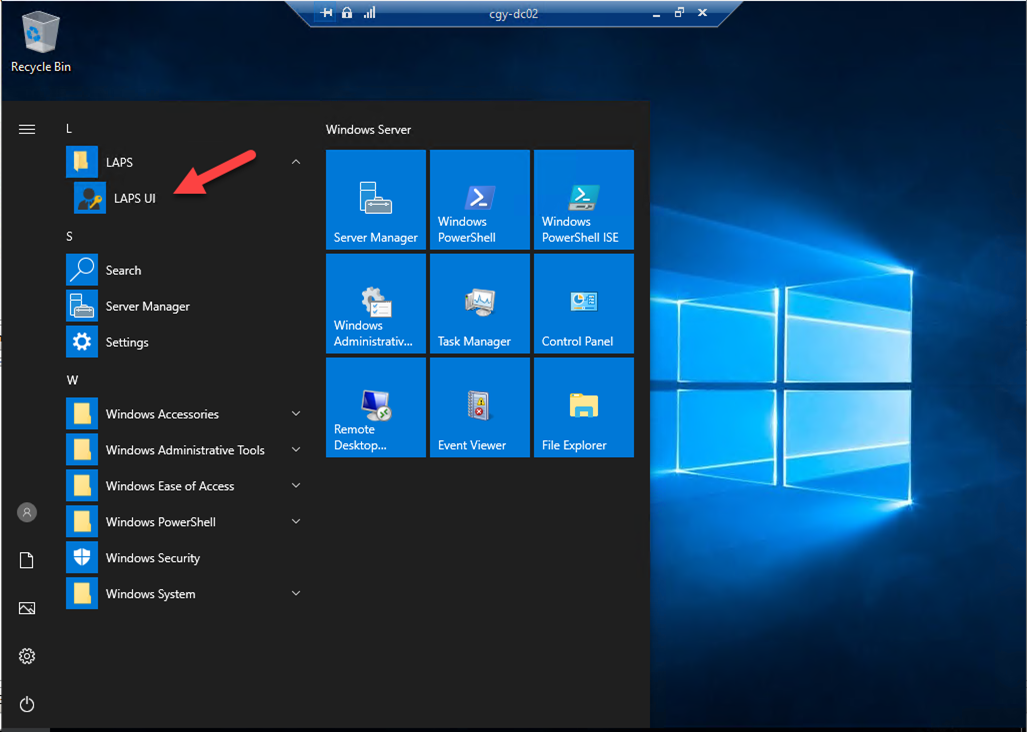
45.Type the computer name (member of Server OU), click Search.
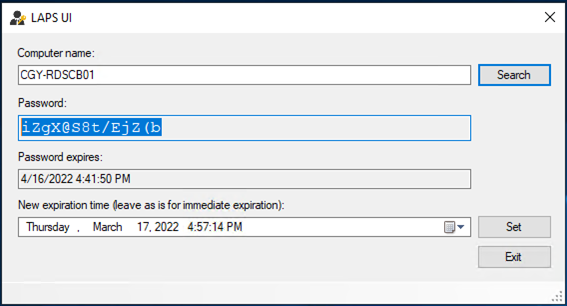
46.You will notice LAPS changed the password of the local administrator account.
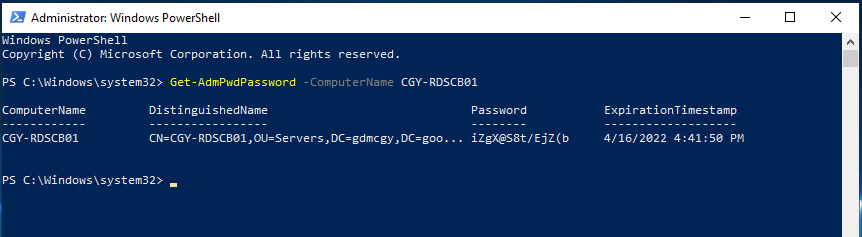
47.You also can run below PowerShell cmdlet to retrieve the local administrator password.
Get-AdmPwdPassword -ComputerName CGY-RDSCB01 |fl
Hope you enjoy this post.
Cary Sun
Twitter: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Author: Cary Sun
Cary Sun has a wealth of knowledge and expertise in data center and deployment solutions. As a Principal Consultant, he likely works closely with clients to help them design, implement, and manage their data center infrastructure and deployment strategies.
With his background in data center solutions, Cary Sun may have experience in server and storage virtualization, network design and optimization, backup and disaster recovery planning, and security and compliance management. He holds CISCO CERTIFIED INTERNETWORK EXPERT (CCIE No.4531) from 1999. Cary is also a Microsoft Most Valuable Professional (MVP), Microsoft Azure MVP, Veeam Vanguard and Cisco Champion. He is a published author with several titles, including blogs on Checkyourlogs.net, and the author of many books.
Cary is a very active blogger at checkyourlogs.net and is permanently available online for questions from the community. His passion for technology is contagious, improving everyone around him at what they do.
Blog site: https://www.checkyourlogs.net
Web site: https://carysun.com
Blog site: https://gooddealmart.com
Twitter: @SifuSun
in: https://www.linkedin.com/in/sifusun/
Amazon Author: https://Amazon.com/author/carysun