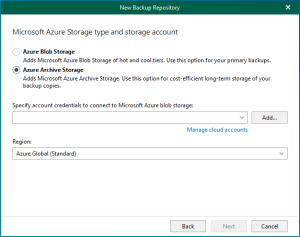
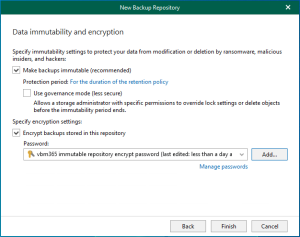
Let's walk through the steps to perform a Physical to Virtual machine (P2V) conversion...
Uncategorized
Vulnerability in this Veeam Backup & Replication component allows unauthorized users to obtain encrypted...